Frequently Asked Questions
- Digital Transformation
- Digital Transformation Frequently Asked Questions
AUC Device Management Project
About DMS
The AUC Device Management Project is an institutional strategic direction aimed at managing and securing AUC digital assets and their configurations, through a centralized system. The actions involved in the AUC Device Management project include joining AUC devices to a centralized Device Management Service (DMS), implementing user access controls, assigning unique device names, enabling security logs and settings, and remotely pushing updates and patches.
The AUC Device Management project is important because it enables AUC to efficiently manage, govern, and secure its digital assets. This long-standing practice, implemented in institutions and universities for many years, serves as a foundation for essential security, management, and compliance standards and laws that AUC needs to comply with.
- Joining DMS helps safeguard AUC assets from various security threats (malicious software, hacking, ransomware, etc.).
- It serves as a foundation for keeping track of AUC's hardware and software resources.
- Joining DMS provides a starting point for managing and securing device configurations.
- It establishes a foundation for verifying the integrity and authenticity of software used by AUC.
- Joining DMS enables the implementation and enforcement of security controls on AUC devices.
- It allows for the timely application of patches and security measures to address vulnerabilities on AUC devices.
- Joining DMS facilitates the management and enforcement of encryption measures on AUC device hard drives.
- By limiting user changes at the system level, Joining DMS helps mitigate potential technology errors.
Device Management means taking technical actions to properly manage AUC assets. These actions include:
- Users are not allowed to freely install or uninstall programs without permission.
- When using AUC devices, users must use their AUC login information rather than any local or temporary accounts.
- Each device is given a specific name that helps AUC identify and keep track of it.
- AUC ensures that devices have their operational and security logs, configurations, and settings properly enabled.
- Users are not allowed to uninstall or disable any security programs that are installed on the device.
- AUC remotely delivers updates for both operational and security-related programs on the device.
DMS Support and Assistance
For Support-related Issues:
If you experience a technical issue or require support related to the DMS, please email support@aucegypt.edu. The central IT team will review your request and address it promptly. If further discussions with requester are required, the request will be sent to techsupport@aucegypt.edu to manage and forward the request to higher management, if needed, in line with the DMS Privileged Access Management Process.
For Software Installation or BigFix/Catalog Requests:
For any inquiries or requests related to software installation, BigFix, or the software catalog, please review our Software Solutions page for details on the software that can be installed promptly on DMS-joined machines, in addition to our approved list of software that you can install after submitting an installation request on our IT support portal. The team will ensure your request is processed in alignment with the DMS policies.
For General Inquiries About the Concept or Need for DMS:
If you have questions about the broader DMS framework or its security implications, please reach out to infosec@aucegypt.edu for further clarification.
Following our standard SLA: if the request is related to a normal DMS support request, it will be addressed within one business day. Escalation requests are handled as service requests and will be processed within three business days.
DMS Eligibility and Enrollment
AUC DMS is planned to cover all AUC devices/assets, including those running Windows, Mac and Linux operating systems. For devices that cannot be directly joined, Mobile Device Management tools will be used.
Currently, devices not owned by AUC are not required to join the AUC DMS. This practice is specific to AUC digital assets only. However, this policy may evolve in alignment with best practices in higher education institutions to ensure robust cybersecurity and data protection.
Yes, as the project is divided into phases to ensure a systematic and efficient process covering all operating systems. Phase one of the project will include Windows-based machines and regular updates and instructions will be shared about the following phases.
The AUC Device Management Project is an institutional strategic direction to ensure consistent management, governance, and security of AUC assets. Opting out of the project is not possible as it is essential for maintaining a secure and compliant environment.
The time it takes to add a machine to the DMS can vary depending on several factors, including the specific data and software you have on the machine. In general, the process can take from 30 to 60 minutes. However, this is only an estimated timeframe.
Before DMS Enrollment
Generally, no special preparations are required before joining the DMS. However, outdated devices may need some adjustments beforehand. We recommend consulting the Central IT Team to ensure your device is up to date and ready for enrollment.
While joining the DMS typically doesn't result in data loss, we strongly recommend that you always back up your important files and data. It is the user’s responsibility to ensure their data is securely backed up before enrollment.
Joining the DMS will not affect your software, but DMS administrators might restrict certain software installations to maintain standardized environments and prevent unauthorized applications from being installed. This is done to enhance security and reduce the risk of malware or unapproved software being introduced to the network.
When you join the AUC DMS, the AUC device will follow AUC-approved configuration and settings. This may result in some changes to the computer settings and profiles. However, your personal files and settings will typically remain intact.
Joining the DMS should not impact your internet connection or general network settings. The device will retain its network configurations, and internet access should remain unaffected.
No, individual account creations or password changes are not allowed on DMS-joined devices to maintain a standardized and controlled environment. Users are required to use their AUC credentials to access any DMS-joined devices.
After DMS Enrollment
Once your computer is joined to the AUC DMS, the login screen will display the DMS name as an option. Select it, and then enter your AUC email credentials (username and password) to log in. After successful authentication, your computer will load your device-managed user profile and settings.
Yes, as part of the AUC Device Management project, there are limitations on user privileges to install or uninstall programs on AUC digital assets. This is to ensure security and compliance with AUC policies. Users will need to request assistance from IT support for software installations or removals.
If your device-managed account gets locked out due to multiple incorrect login attempts or other security reasons, you'll need to open an IT Ticket to unlock your account. The support team will verify your identity and help you regain access.
Device-managed accounts and data are generally secured through centralized authentication and access controls managed by the AUC's IT team. Strong password policies, encryption, and other security measures are implemented to protect device-managed resources.
The AUC Device Management Project implements privileged access management solutions for IT and DMS Administrators. It includes monitoring access, establishing defined processes and responsibilities, setting boundaries, and implementing change management procedures to mitigate the risk of abuse. By implementing these controls and measures, AUC addresses the issue and ensures the security and integrity of its systems and assets.
DMS Data Privacy
The device management project is based on two state-of-the-art solutions in the market; CrowdStrike and BigFix. CrowdStrike Falcon ensures privacy protection through data minimization, encryption, and strict access controls. As a cloud-based solution, CrowdStrike Falcon complies with regulations like GDPR and CCPA, providing transparency and regular audits to uphold data security and minimize risks. As for BigFix, it is securely hosted on-premises and is managed by a restricted group of authorized administrators. BigFix's encryption standards, which comply with FIPS 140-2, meet federal requirements, ensuring data protection without compromising user privacy.
Knowing what is attached to the network is critical to identify and remediate security vulnerabilities. Data below is collected to determine if there is malicious behavior:
- Hardware data such as device model, serial number, manufacturer, Processor type and speed, RAM Size, storage capacity.
- Operating System data such as Operating system version, last boot time, language, installed applications.
- Network data such as DNS name, IP address, MAC address.
- Details about the username that has logged in on the machine, what programs are run, what links they accessed and the names of programs and files that are read or written, and records network activity. The content of files and links are not collected or accessed. In case of a security vulnerability, online activity may be monitored to detect and mitigate direct and explicit threats to the computer system.
Device management system does not grant access to the contents of your emails, chats, files, meetings, passwords, contacts and events.
No, the tools only record and process details about programs that are run and the names and directories of files that are read or written, but not the contents of files.
- Report and automatically address suspicious activities and security threats on AUC devices.
- Timely apply security patches and measures to address vulnerabilities on AUC devices.
- Manage and secure device configurations and software updates.
- Implement and enforce security controls on AUC devices.
- Facilitate the management and enforcement of encryption measures on AUC device hard drives.
- Mitigate potential technology errors by limiting user changes at the system level.
- Implement user access controls.
- Identify and keep track of AUC's hardware and software resources.
- Improve system performance and user experience.
- Verify the integrity and authenticity of software used by AUC.
BigFix is securely hosted on-premises and is managed by a restricted group of authorized administrators while CrowdStrike provides secure storage on its cloud servers for the data it collects, and AUC retains ownership of the data.
To protect user data, AUC employs the following technical and organizational measures:
- Access Control: Role-based access controls ensure only authorized personnel can access sensitive data.
- Encryption: Data at rest and in transit is encrypted to protect against unauthorized access.
- Confidentiality Agreements: All AUC employees, including authorized IT administrators, sign confidentiality agreements.
- Training and Awareness: Regular privacy and security training is provided to system administrators.
- Audit Logs: Audit logs are maintained to ensure authorized employees access data only on a need-to-know basis.
Data retention vary, but typically, data is retained for around six months to allow for threat analysis and compliance reporting. After this period, the data is securely deleted to prevent unauthorized access.
Multi-Factor Authentication (MFA) Implementation
MFA is a security feature that adds an extra layer of protection to your login process. It requires more than just your username and password for accessing your account, ensuring higher security. By implementing MFA, only you, as the account owner, with the correct combination of credentials, can successfully log in. This step is essential to protect your account and sensitive information from unauthorized access.
MFA is planned to be applied to all faculty, staff, and students. Currently, the MFA is applied to all faculty, staff and students
After the MFA is applied to your account, follow these steps for successful authentication:
| |
| |
| |
|
The current settings require re-authentication every 90 days. Kindly note that you will need to re-authenticate on each device and each browser you use. Please refer to the next question for more details.
Yes, you will need to authenticate for each browser (chrome, safari, etc.) or device (PC, phone, tablet, etc.) that you use to log in to your account. Each browser on each device that you use will require MFA authentication.
To ensure a smooth transition to MFA, please review and update your contact information. Make sure your email addresses and phone numbers are accurate and up-to-date in our system. We have prepared instructions on how to update your contact information (Dated March 1, 2023) that should help you if needed.
If you can't receive a call or SMS, or prefer an alternative authentication method that doesn't require a mobile network or valid SIM card, you can use the Microsoft Authenticator app. We have created a detailed guide on how to set up your account and authenticate using the app (PDF).
Immediately visit your MFA authentication settings screen and sign out from all your devices. Your next important step will be to change your AUC password. If any suspicious activity is monitored, report instantly an incident by sending an email to IT Support or information security.
Anyone who is traveling abroad should use the Microsoft Authenticator app on their device. Text messages and phone calls may not be accessible during travel. We have created a detailed guide on how to set up your account and authenticate using the app.
You can visit your MFA authentication settings screen to add a new sign-in method, change your default sign-in method or sign out from all your devices.
MFA provides an added layer of security, protecting your account and sensitive information from unauthorized access. By implementing MFA across the entire AUC community, we are committed to maintaining the highest level of security for our systems and ensuring the safety of all accounts.
If you have any additional questions or require support with Multi-Factor Authentication, please open an IT ticket by sending an email to IT Support or information security. Our support team is ready to assist you and address any concerns you may have.
IT Help Desk
Ensure that the clearpass icon is open at the bottom right of your screen. If you cannot locate it, open the program from the start menu.
- Right-click on the network icon at the right corner of your toolbar
- Select Open Network and Internet Settings
- Select Change Adaptor Options
- Right-click on Ethernet
- Select Properties
- Select Authentication
- Select Additional Settings
- Select Replace credentials or Save Credentials
- Enter your AUC email username and password
- Click Ok on all open windows till you reach Ethernet
This is a browser error. Either use a different browser or clear the cache of your browser as follows:
- Open Chrome or Firefox
- On new tab, for Chrome click Ctrl+H, for Firefox Ctrl+Shift+Delete
- In the clear browsing data box, choose advanced in the case of Chrome and use the menu at the top to select the amount of data that you want to delete. Choose from the drop-down list clear the following items from the past week. Check all the boxes including cookies and other site data, and cached images and files except media licenses and passwords (if you have any saved)
- Click on clear browsing data
- Restart the browser
If you receive the error unauthorized access upon login, follow the below steps:
- Clear the cache of your browser as follows
- Open Chrome or Firefox
- On a new tab for Chrome, click Ctrl+H; for Firefox Ctrl+Shift+Delete
- In the Clear browsing data box, choose Advanced in the case of Chrome and use the menu at the top to select the amount of data that you want to delete. Choose from the drop-down list clear the following items from the past week
- Check all the boxes, including Cookies and other site data, and cached images and files except media licenses and passwords (if you have any saved)
- Click clear browsing data
- Restart the browser
CANVAS
Desktop Technical Support
Click on Ctrl+Alt+Delete and Lock. When you want to unlock your computer, type in your password. On Windows, you can also press the Windows key and L for easy access.
A print queue is a list of all documents that are scheduled to be printed, and you will want to clear this if you no longer want to print all of the documents. To clear your print queue, simply locate your printer settings and right-click on the correct printer. You will then see a list of all documents, which you can then right-click and cancel.
- Press the Windows button+R
- Type:\\10.2.70.11
- Press ok
- In the generated window, type:
auc\username (your AUC email username) without @aucegypt.edu
Password (your AUC email password)
First, check the computer's power cord to make sure it is completely plugged into the wall socket. If you are using a plug strip, make sure it is completely plugged into the wall socket and that the power switch on the plug strip is turned on. Some plug strips also have a built-in circuit breaker which usually looks like a black or red button near the power switch. Press the button to reset it and see if that solves the problem.
There are many reasons why a computer may just stop working or "freeze". Most of the time there isn't much we can do about it, it is a fact of life that computer programs have become so complex that occasionally users will experience problems even when performing common tasks. When your computer no longer responds to keyboard commands your best bet is to restart the computer.
Microsoft Internet Explorer users can go to 'Tools' (or the little cog icon in the top left), then go to 'Safety' and choose 'Delete browsing history', you can then choose to delete your Internet cookies. In Google Chrome, go to 'More Tools' and choose 'Clear browsing data.' Firefox users can go to 'History', then choose 'Clear recent history.'
Students, faculty, and staff can schedule an appointment with the IT desktop technical support representative to help troubleshoot their personal laptop and desktop application problems for both Windows and Mac IOS platforms. This service also helps in software installations, including MS Windows.
- Provide on-site analysis, identification, and resolution of difficult desktop problems for end-users, including MS-Windows operating system and application installation.
- Test, evaluate, and assess new IT equipment to ensure the quality of products purchased by AUC.
- Inspect the new equipment to ensure that AUC received the right spec of purchased products from vendors.
- Support remote installation and give desktop technical support for remote users (limited now).
- Assist limitedly with hardware and technical support advice.
- Prepare reports regarding old IT equipment transferred to the AUC warehouse before re-distribution to the department for reuse when needed.
VPN Account Creation
To create a VPN account, fill in this form and wait for a creation notification email to set up your account within two business days.
After receiving a VPN account creation notification email, activate your account by following the steps below:
- Open forticlient.com and download the forticlient for your OS
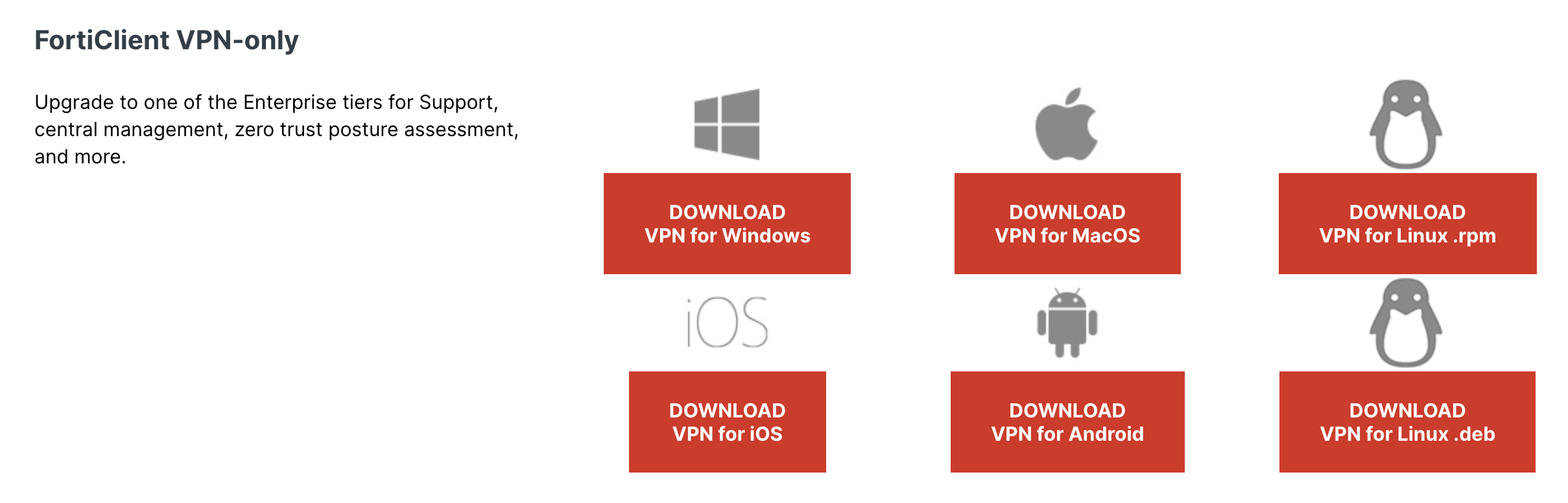
N.B.: Make sure to select Forticlient VPN-only
2. Set the connection name as you want
3. Set VPN type to SSL VPN
4. The server address is aucvpn.aucegypt.edu and the port: is 8090
5. Use your email username (your email without @aucegypt.edu) and password as your initial credentials and log in to have a successful connection
Microsoft Windows
You can get your Windows installed following these steps
1. Open a ticket on IT Self Service Portal schedule an appointment with a technical support representative
2. Visit IT Support for physical installation
You dont need your windows product key anymore,
Please follow the following steps to install/activate your windows again:
1. Open a ticket on IT Self Service Portal schedule an appointment with a technical support representative
2. Visit IT Support for physical installation
Microsoft Office
All students, faculty and staff are eligible to install Microsoft Office 365 for free.
To access all Microsoft 365 apps and folders and OneDrive shared files, sign in to Microsoft 365 Portal using your AUC email credentials
Note: You must be logged in to access your product
Microsoft Teams
Visit teams.microsoft.com, you will be prompted to enter your AUC credentials. Your office365 cloud portal appears. Open Microsoft Teams, and click on the download desktop app icon in the left navigation pane. This will download the app to your computer, and you can install and activate it on your desktop.
A team is a collection of people, conversations, files, and tools all in one place. A channel is a discussion in a team dedicated to a department, project, or topic. Click teams and select a team. Pick a channel to explore the conversations, files, and other tabs.
Click here for a video tutorial.
To start a conversation with the whole team, click on teams, pick a team and channel, write your message, and click send. If you need to make a conversation with a person or group, click on a new chat, type the person or group's name in the to field, write your message, and click send.
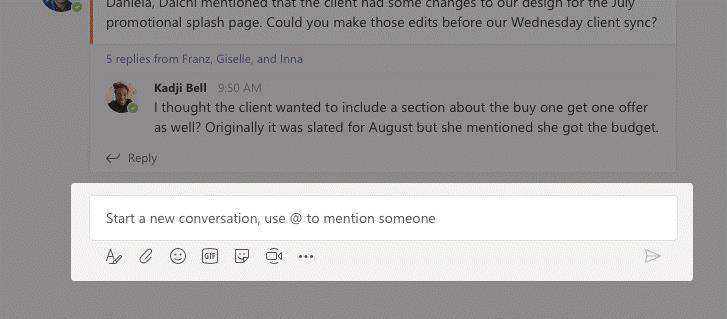
Click on meet now under the area where you type a message to start a meeting in a channel. If you click reply, then meet now; the meeting is based on that conversation. Enter a name for the meeting, then start inviting people.
Click here for a video tutorial.
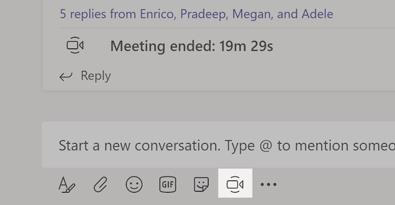
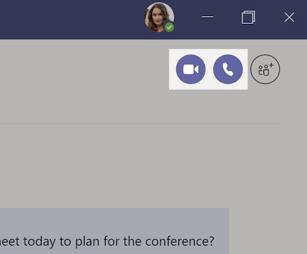
Click on a video call or audio call to call someone from a chat. To dial a number, click on calls on the left and enter a phone number. View your call history and voicemail in the same area.
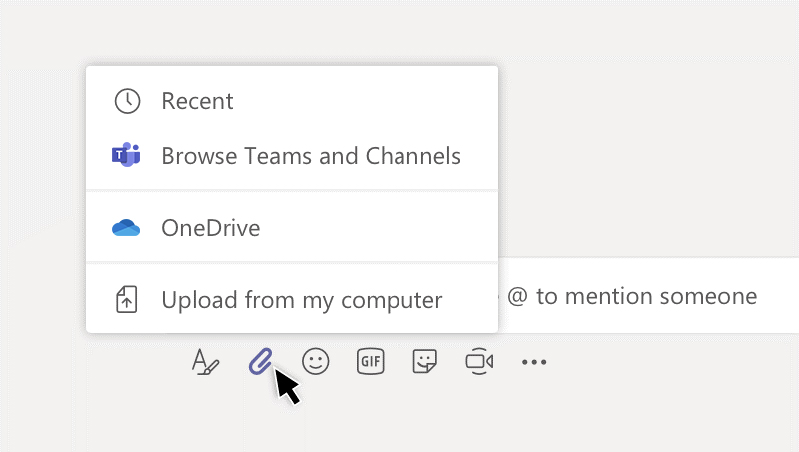
Click on attach under the box where you type messages, select the file location and then the file you want. Depending on the file's location, you will get options for uploading a copy, sharing a link, or other ways to share.
Click here for a video tutorial.
You can click on files on the left to see all files shared across all of your teams. You can also click on files at the top of a channel to see all files shared on that channel. Click on more options next to a file to see what you can do with it. You can instantly turn a file into a tab at the channel's top for quicker access.
1. Select teams. Then go to the team on your team list.
2. Select more options. Then add a member.
3. Enter the guest's email address. Anyone with a business or consumer email account, such as Outlook, Gmail, or others, can join your team as a guest.
4. Add your guest's name.
5. Click add.
Yes, find below the available Microsoft Teams videos classified by topic:
Quick Start
Intro to Microsoft Teams
Set up and customize your team
Collaborate in teams and channels
Work with posts and messages
Upload and find files
Start chats and calls
Manage meetings
Set up and attend live events
Explore apps and tools
Manage team schedules with Shifts
Manage your activity feed
Teams on the go
Visual Studio
For students and staff, follow the instructions below to activate and download Visual Studio:
- Click here to download visual studio from Microsoft Azure Dev Tools for Teaching
- You will be prompted to log in to your Office 365 account, enter your AUC credentials
- After successful login, to the Azure for education page, on the left pane under Learning Resources, choose Software
- In the search bar, type Visual Studio, choose the option that matches your PC configuration and Operating system
For further support, post an IT service request on the IT Service Management Portal and choose PC/Laptop software category.
Zoom Video Conferencing
1. Open Zoom any browser and type
2. If you have a meeting ID, choose join a meeting to connect a meeting in progress.
3. Click on sign-in to configure your account.
4. Click on sign in with Google.
5. You will then be directed to enter.
1. Sign in first, as mentioned above.
2. Choose my account from the upper right side of the page.
3. Select meetings from the left column under personal.
4. Click on schedule a new meeting.
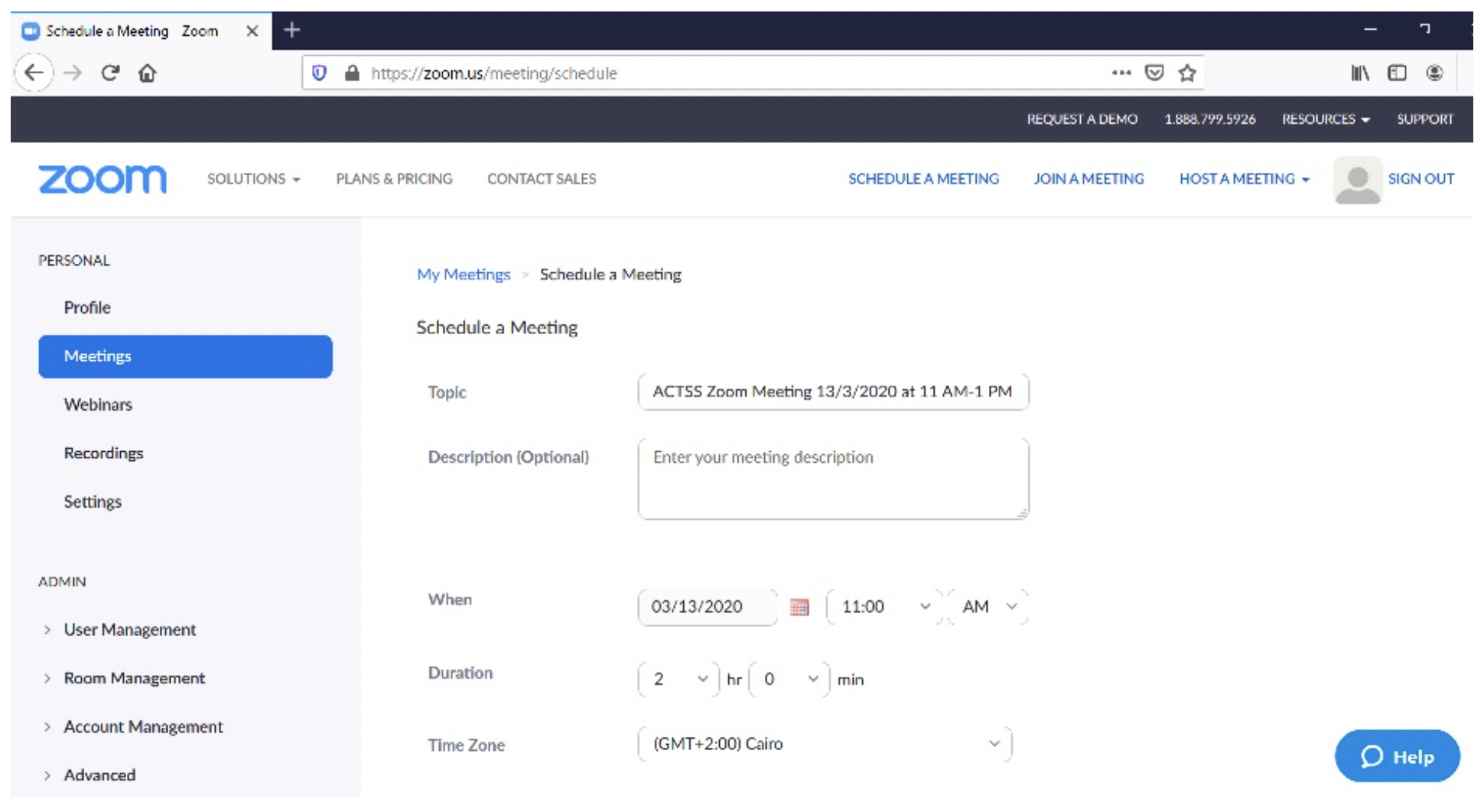
5. Topic: type in the title of the meeting.
6. When: choose the date and the time of the invitation.
7. Duration: choose how many hours the meeting will be held.
8. Fill up all the data as per the below screenshots then click on save.
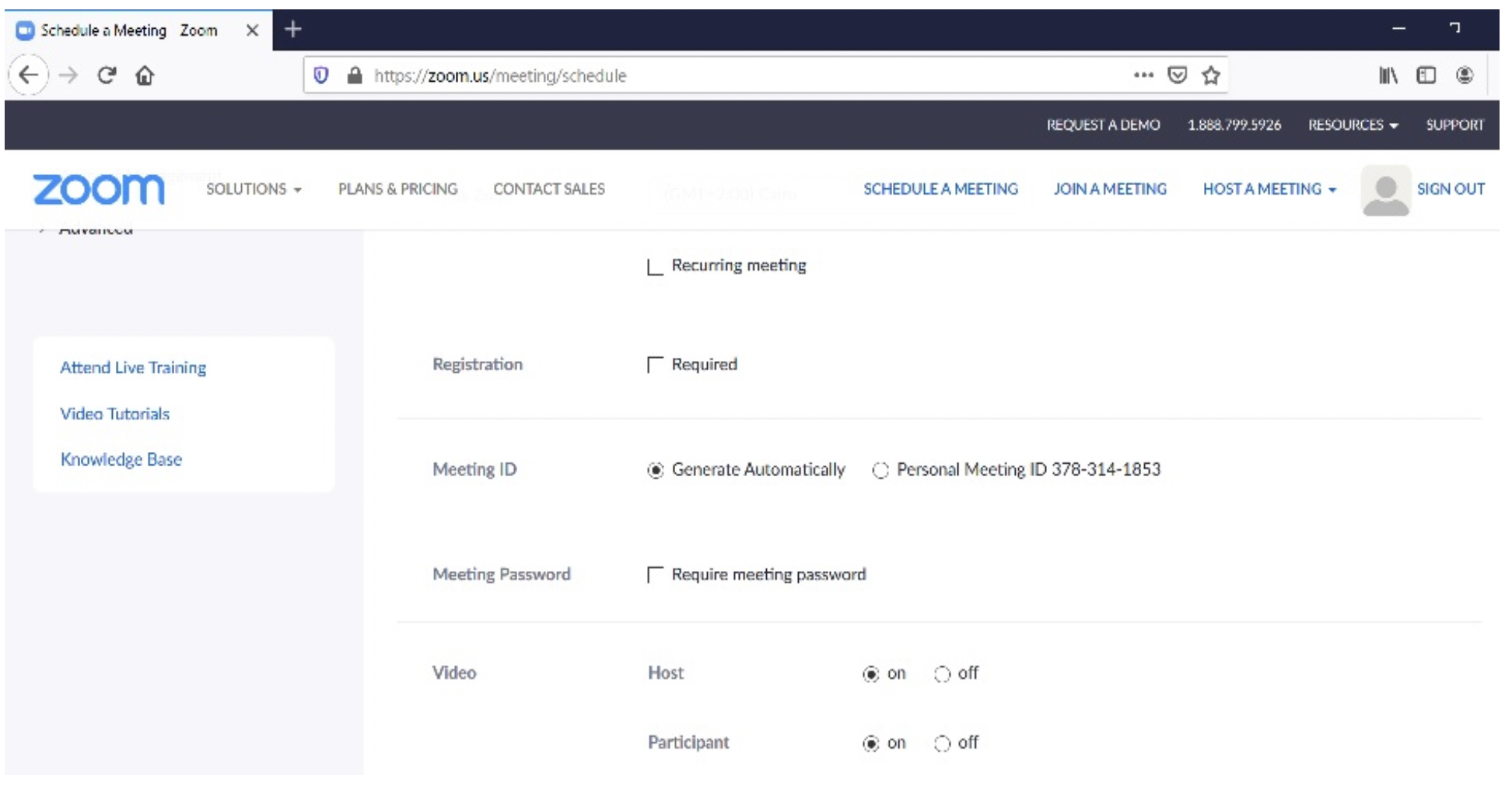
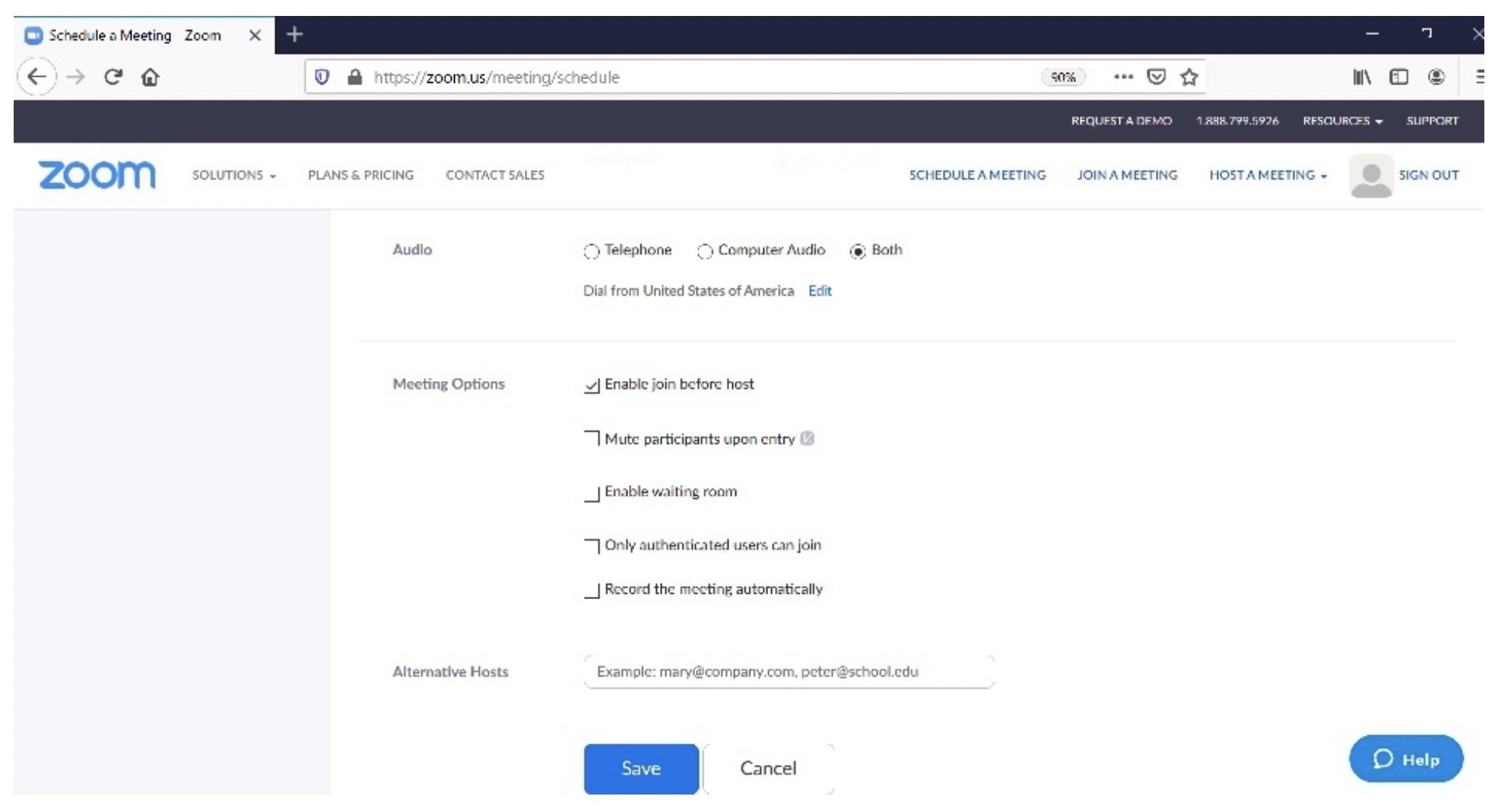
9. The meeting invitation will appear as shown below:
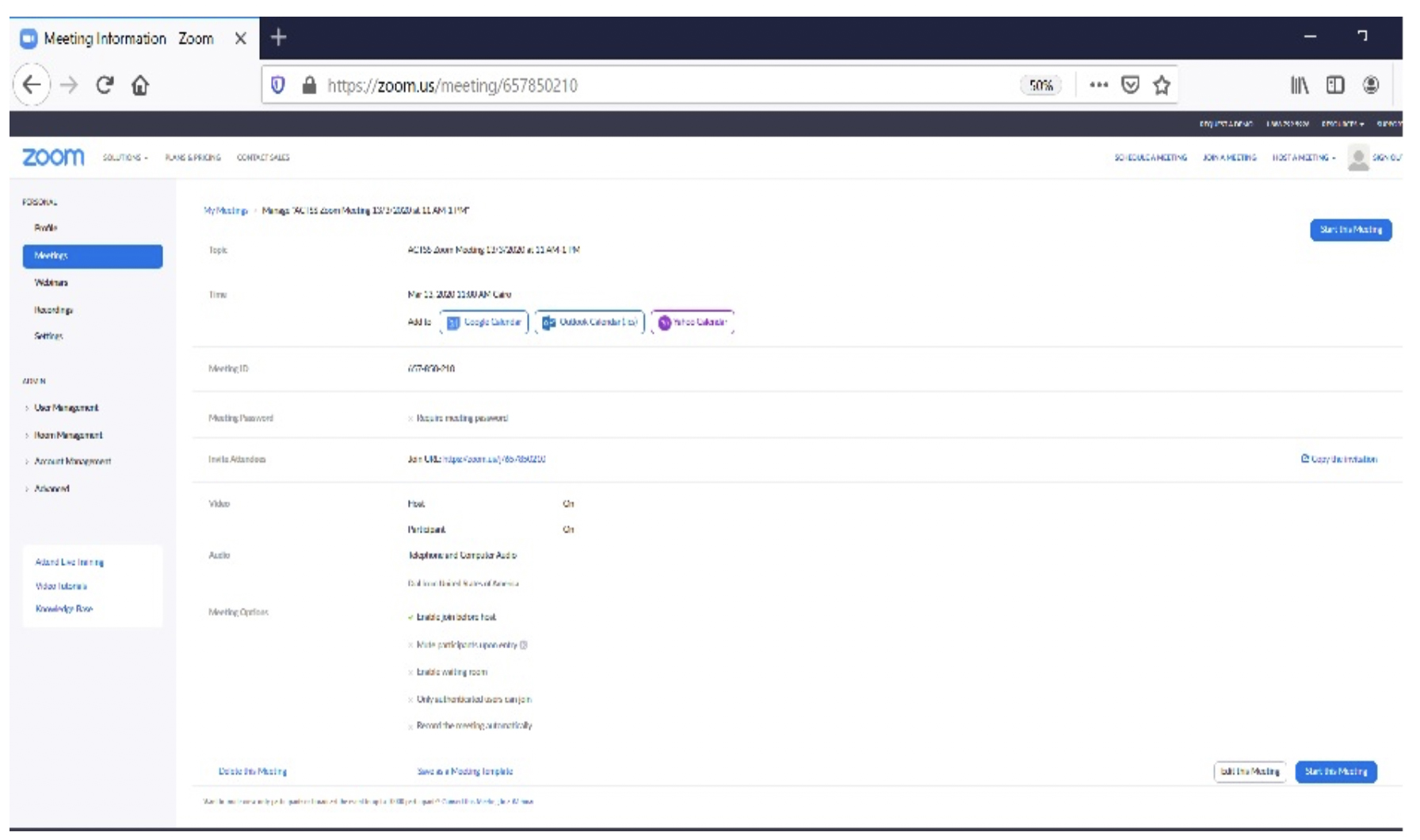
10. Go to invite attendees then select copy meeting invitation as per the below screenshots and send it via email to the meeting attendees.
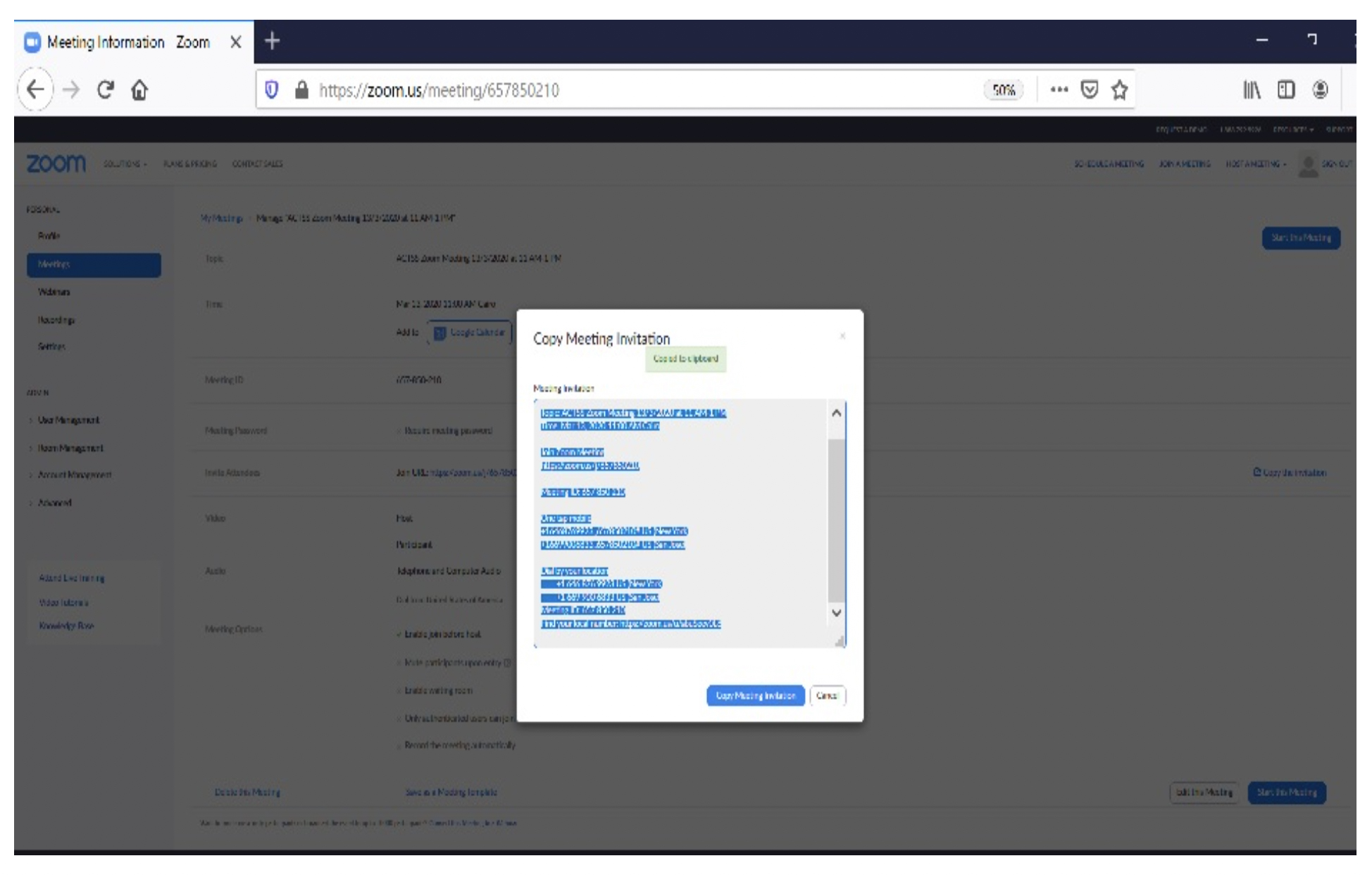
The invitation to a zoom meeting will be as follows:
Topic: Meeting
Time: May 9, 2017, 2:00 pm, Cairo
Join from PC, MAC, Linux, IOS or Android here.
Meeting ID: 123 456 789
Or iPhone one-tap (US Toll): +14086380968, 123456789# or +16465588656, 123456789#
Or telephone: Dial +1 408 638 0968 (US Toll) or +1 646 558 8656 (US Toll)
Zoom International Dial-in Numbers can be found at this link.
Or an H.323/SIP room system:
H.323:
162.255.37.11 (US West)
162.255.36.11 (US East)
221.122.88.195 (China)
115.114.131.7 (India)
213.19.144.110 (EMEA)
202.177.207.158 (Australia)
209.9.211.110 (Hong Kong)
If you are using a desktop or laptop:
1. Open the invitation email and click on the first provided link in the invitation e-mail:

Zoom webpage will open in a new tab in your browser.
2. For first time access to zoom application, select launch application/download here or select run/save at the bottom of the page
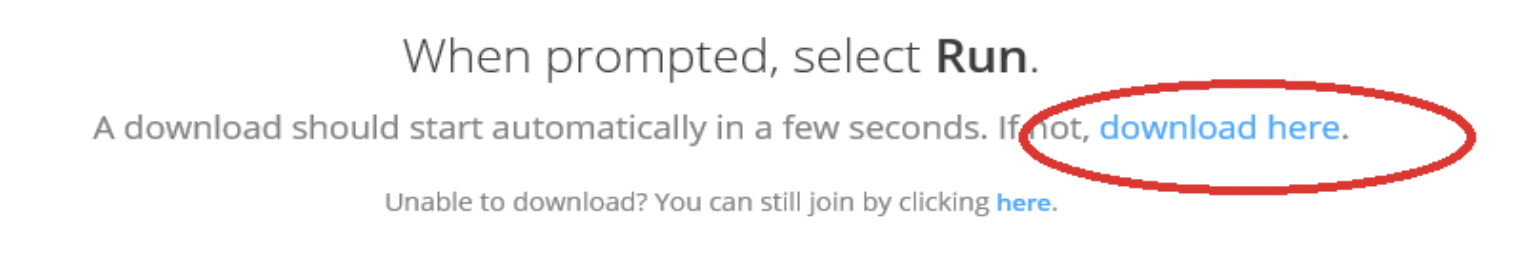
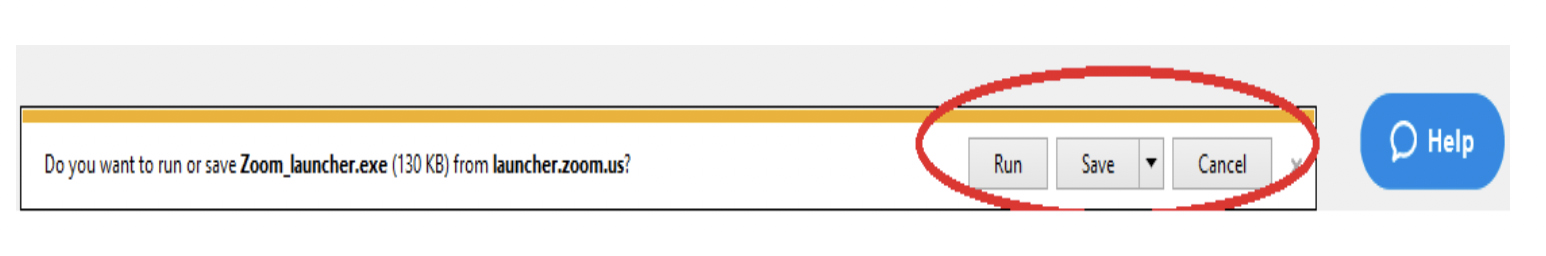
3. Open the Zoom icon.
4. Click on join a meeting.

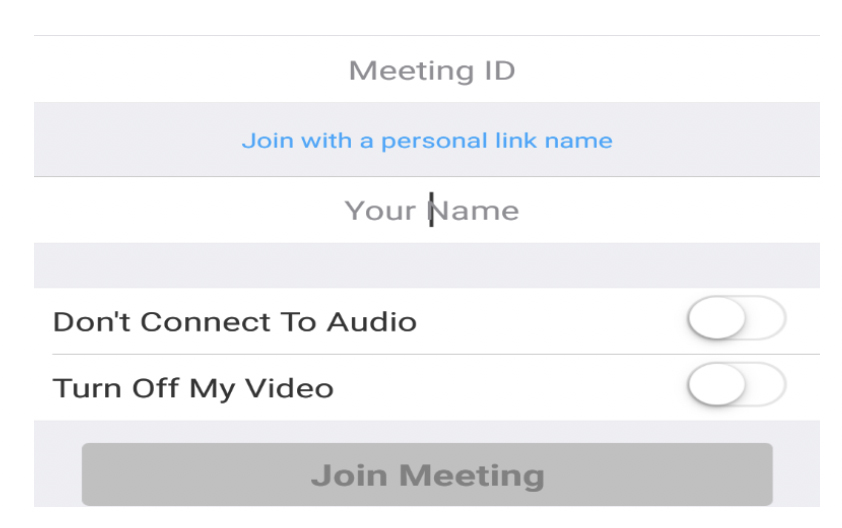
5. Type down the meeting ID as seen below.
6. Then type in your name in the Enter your name field.
7. Select remember my name for the future meeting to save your name for all upcoming meetings.
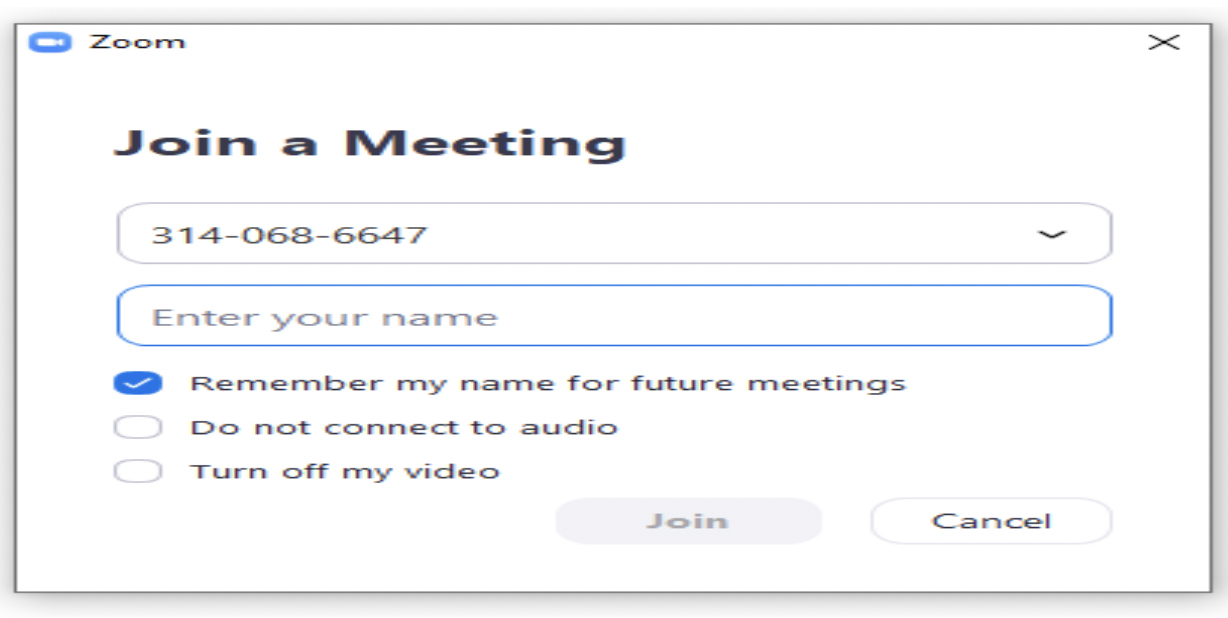
8. To invite more people to join by email, use the invite icon or send them an SMS with the meeting ID number.
![]()
If you are using Android/iPhone/Tablet/iPad:
1. Download the Zoom Cloud Meetings application from Apple App Store or Google Play Store.
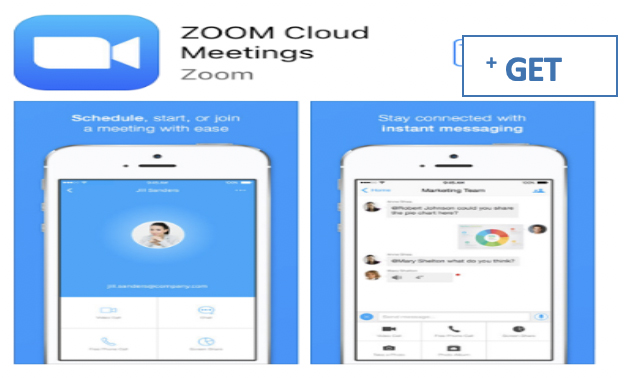
2. To join a meeting, you can either select join a meeting and then enter the meeting ID number or you can directly click on the URL sent to you via email.
3. To invite more people to join, click on the Participants icon on the bottom then click invite. You can invite via SMS or by copying the URL.
Yes, find below the available Zoom Youtube videos classified by topic. Click on the links below to watch these videos.
- Sign in to your Zoom account on the web browser by following the below instructions:
- Go to zoom.us
- Click on the Sign In located in the top right corner.
- Choose the Sign in with Google option.
- Enter your AUC email credentials, and You are in!
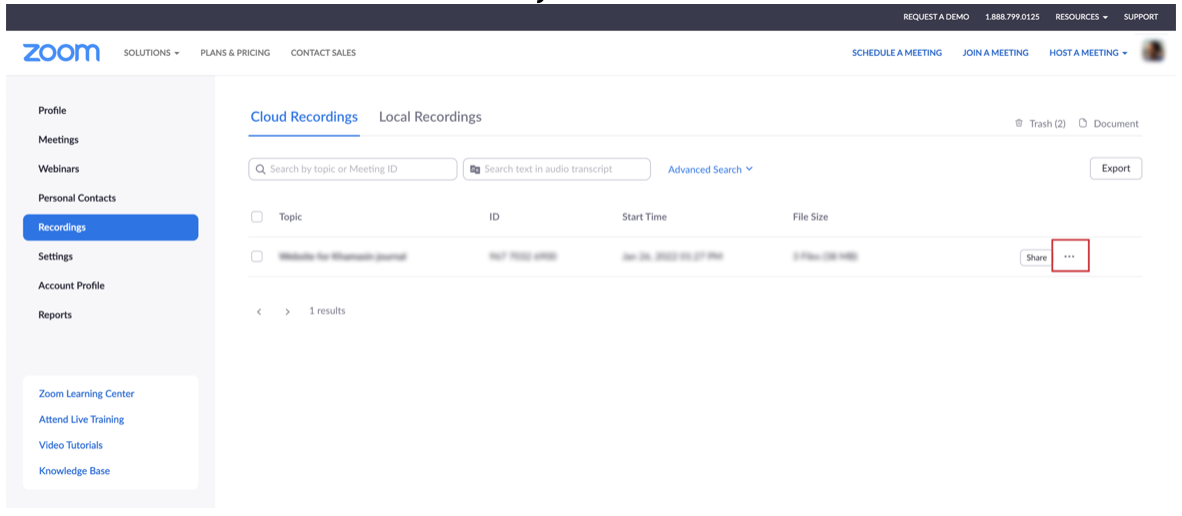
2. Select the Recordings category on the left. Under the Cloud Recordings tab at the top, you will have a list of the recordings you saved to the cloud. Click on the More button next to the item you wish to download.
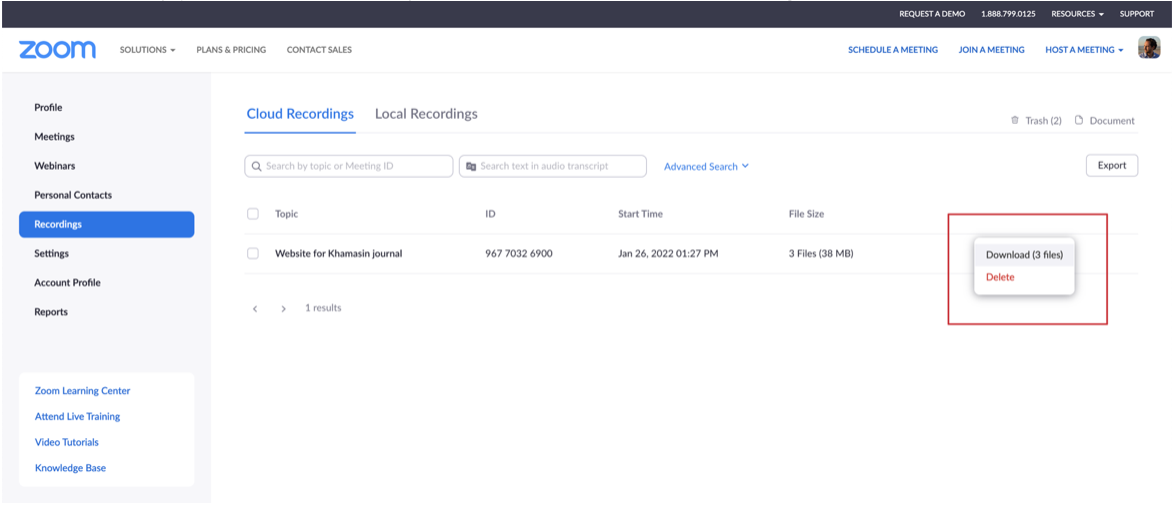
3. From the available options, select the Download option to start downloading all your recordings related to the selected topic.
4. You can also export a list of cloud recordings or export a CSV of viewing analytics.
- Sign in to your Zoom account on the web browser by following the below instructions:
- Go to zoom.us
- Click on the Sign in button located in the top right corner
- Choose the Sign in with Google option
- Enter your AUC email credentials, and you are in!
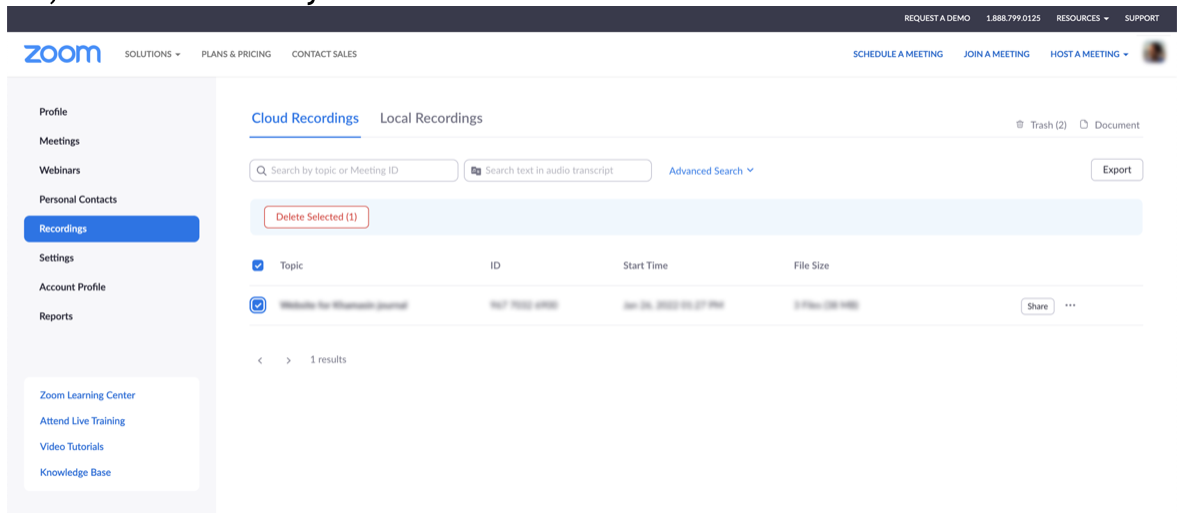
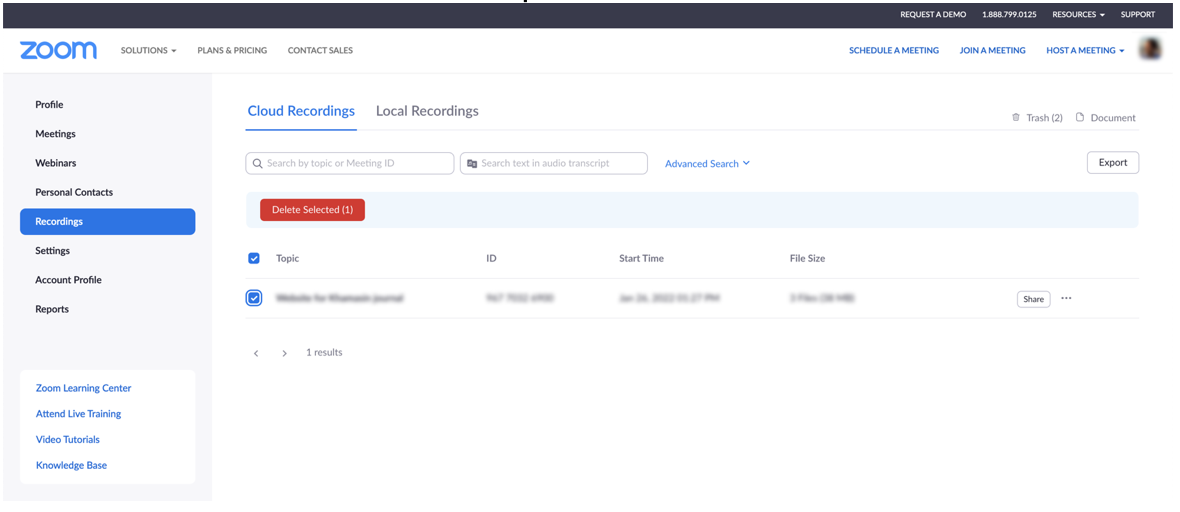
2. Select the Recordings category on the left. Under the Cloud Recordings tab at the top, you will have a list of the recordings you saved to the cloud. On this list, choose the items you wish to delete.
3. Click on Delete Selected button to proceed.
Remote Access to Campus Computer Labs
Yes, if you want to work on any of the machines on campus’ computer labs, all you need to do is to download the RealVNC Software from here and refer to your course instructor/TA or Lab administrator to receive an invitation to create a RealVNC account. RealVNC software works across all devices and operating systems including Windows, macOS, iOS, Android, and Linux ensuring a secure and reliable remote desktop connection.
- Architecture Engineering Lab
- Computer Science Engineering Lab
- Construction Engineering Lab
- Electronic Engineering Computer Lab
- GAPP labs
- Jameel Building Computer Lab
- Mechanical Engineering Lab
- Petroleum Engineering Lab
- Physics Lab
- Psychology labs
- PVA labs
- UACT labs
The above list will be updated once new locations are available.
1. Install or run VNC Viewer and sign in using your RealVNC account credentials. You should see the remote computer appear in the AUC team.
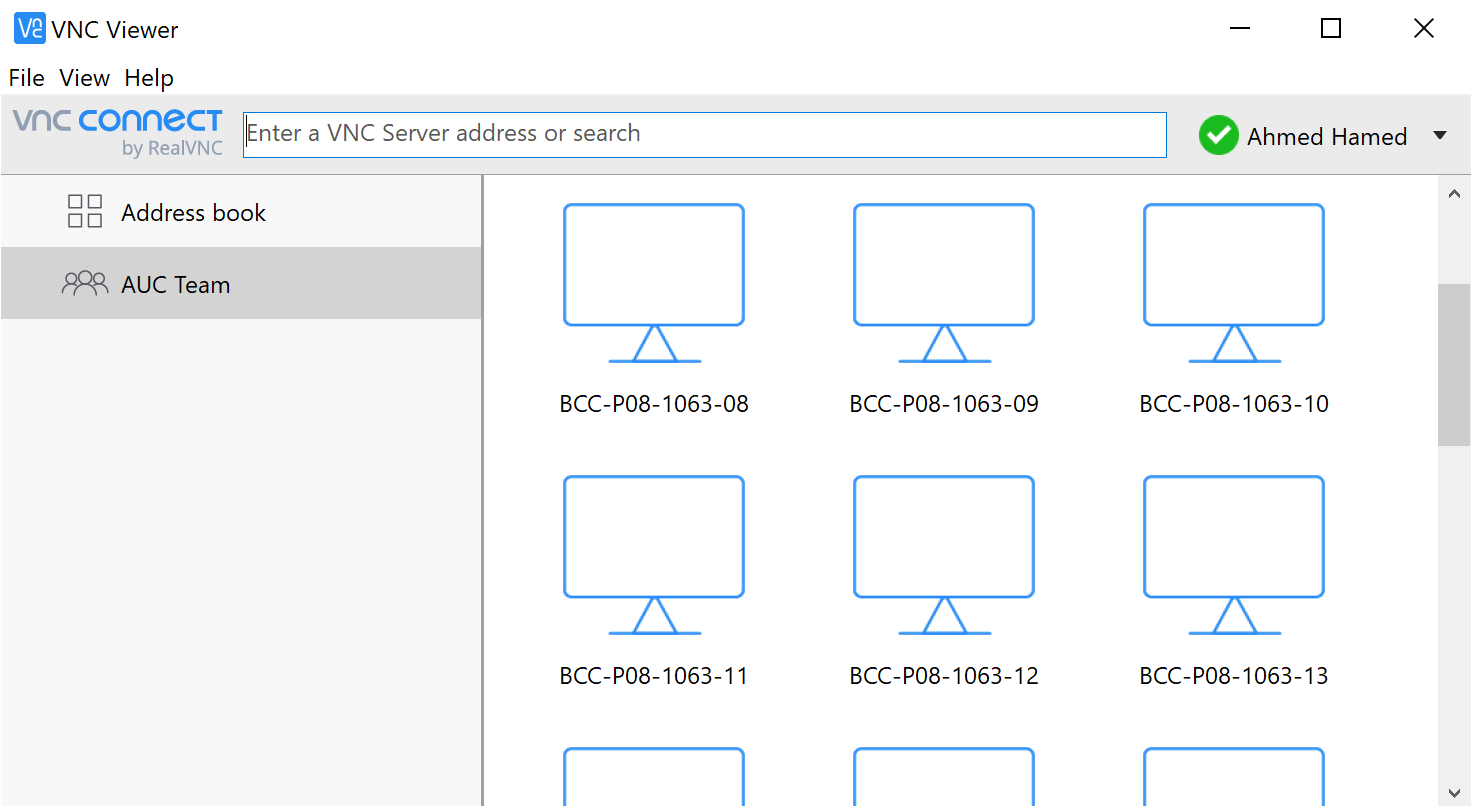
2. Click or tap to connect. You are prompted to authenticate to VNC Server.
3. Enter the username and password that you will receive from the Lab supervisor.
Google Chat
- Download the new mobile app for Android or iOS.
- Download the new standalone desktop app if you have used the classic Hangouts Chrome extension or app. You can access the desktop app from a prompt that appears on chat.google.com.
- On February 7, 2021, refresh your Gmail to get the new Chat in Gmail experience.
You can continue recent conversations from classic Hangouts in Google Chat. Over time, older conversations from classic Hangouts will also migrate to Google Chat. All previous chat history from classic Hangouts will be accessible in Gmail.
- Google Voice and Google Fi are not available through Chat. If you already have a Google Voice account, you can either access Google Voice, select Voice from the App launcher or download the Google Voice app (Android, iOS)
- Google Fi users must use the default SMS app on their mobile devices to send and receive SMS messages. If you start rooms in Chat with the option for threaded conversations, these rooms will not appear to people who still use classic Hangouts.
- Go to the Google Workspace Learning Center for more information about the new Chat.
- The AUC Help Desk is ready to answer your questions by phone at t: +20.2.2615.1200 for any additional assist.
Targeted Announcements
Fill in the following Announcement Request Form with your announcement and the group of students you wish to target.
- All announcements need to be submitted from a departmental email account.
- Announcements can be targeted based on any data element captured on the Banner Information System.
- The submitter receives an email confirmation (same day) as soon as the announcement is processed.
- For any amendments or special requests after submission, email onliness@aucegypt.edu.
Meeting Rooms and Lecture Halls
Send an email to CTMS@aucegypt.edu with your requirements with 48 hours prior to your event time, along with venue, date, time, and exact needs.
Pass by the Library building G029 and borrow a video camera or a power shot camera with your ID, as we do not provide video or standstill pictures shooting. Note that this depends on the availability as the borrowing policy is FCFS.
Send an email to CTMS@aucegypt.edu with your requirements, venue, date, and time, mentioning if this streaming is internal among the AUC campuses only or external, and if so, specify if streaming will be on the AUC website, Facebook or YouTube.
Yes, of course, our staff are on-site with at least 30 minutes before the event time.
Yes, this can be done, but your department must carry out the working staff's transportation and overtime. The transportation fees must be paid at the Library building, room G029, at least one day before the event date.
Assistive Technology
You can reach us by email at assist.tech@aucegypt.edu.
Or pay us a visit at the following locations:
a. Room P145, Prince Alwaleed Bin Talal Bin Abdulaziz Alsaud Hall (HUSS Building), Ahmed Abdel Tawab.
b. Room P003, AUC Library, Fatma Moussa.
You must be an affiliated AUC member (undergraduate student, graduate student, faculty, or staff) with an active AUC email.
Assistive technology services offer many services for students with different abilities.
- Academic documents’ delivery services including:
- Optical Character Recognition (OCR) document scanning in both English and Arabic formats
- PDF files conversion to Word or Braille file formats
- Braille printing services
- Screen Reading Services
- In-class note-taking device rental services
- One-to-one or focus groups training services
For a complete list of assistive technology software and hardware, click here.
All services mentioned in the previous question remain except for Braille printing services.
For library operations during campus closure, check the library's website here.
To access online books though bookshare.org, contact the Center for Student Well-Being.
Post a service request on the IT support portal or email assist.tech@aucegypt.edu.
The assistive technology services offer device rental devices for class note-taking using Braille or MP3 recording. Email assist.tech@aucegypt.edu for more information.
This depends on the number of users requesting the service relative to the number of available devices we currently have. You can keep it for a complete semester unless it is needed by another student when you start coordinating the device exchange.
For more information, email: assist.tech@aucegypt.edu.
- Printed or pdf resources should be clear, without handwriting, underlining watermarks, or bad-quality images.
- Scanned copies shouldn't be inverted pages or two-sided.
- For PDF documents that are password protected, refer back to your instructor.
Below are some tips and tricks:
a. Avoid opening many heavy programs simultaneously that consume your computer memory, such as Word, PowerPoint, Excel, Outlook, etc.
b. Open each program separately, and use the Windows+Insert+F4 key if JAWS hangs after closing it. This key unloads JAWS completely from memory and restarts automatically as a fresh session without the pre-loaded scripts.
c. Weekly clear user temp (%temp%) and Windows Temp (temp)
e. Monthly run disk cleanup utility (cleanmgr)
Call t: +2.2615.1200 to direct you to the technical support specialist.
The assistive technology services at AUC offer a free installation on the student's laptop until he/she graduates from AUC.
Email assist.tech@aucegypt.edu to request a license.
JAWS Reader (Assistive Technology)
Microsoft Word (Assistive Technology)
Microsoft PowerPoint (Assistive Technology)
Email (Assistive Technology)
Banner (Assistive Technology)
Google Classroom (Assistive Technology)
Google Drive (Assistive Technology)
University Phone Sets
When you have a new missed call, the Call Log Key![]() will be illuminated in red.
will be illuminated in red.
You can also find an icon  displayed at the top-right corner of the phone's main screen to indicate new missed calls and shows the number of missed callers.
displayed at the top-right corner of the phone's main screen to indicate new missed calls and shows the number of missed callers.
If the number of missed calls is more than 9 missed calls, the number in the icon  will change to the (+) sign to indicate this.
will change to the (+) sign to indicate this.
To access your call log, click on the Call Log key ![]() . There, you can find your missed calls, answered calls and dialed numbers.
. There, you can find your missed calls, answered calls and dialed numbers.
1. Click on Contacts ![]() to display the directory menu.
to display the directory menu.
2. Click on the Search soft key.
3. Start searching by typing your last name using the phone keypad.
4. Press the Search soft key again to display results.
5. Use the up and down cursor keys to select your desired contact from the list displayed on the screen. For each item on the list, you have the option to call, get more details or add to your contacts using the soft keys.
Click on the Redial key ![]() to immediately repeat your most recent outgoing call.
to immediately repeat your most recent outgoing call.
If you wish, the function of this key can be set to give you access to your list of outgoing calls. To do so, click on the Features soft key, then use cursor keys to select Call Settings. Use the up and down cursor keys to select your desired redial mode.
The forward functionality redirects unanswered received calls to another extension or an external number. To forward your calls to another number:
- Click on the Forward Call key

- Enter the phone number or extension to which you wish to forward your calls, then click on the OK Soft key.
Click on the Hold soft key ![]() . The phone displays On-Hold before the call information, and the held call displays the below icon.
. The phone displays On-Hold before the call information, and the held call displays the below icon.
If you are on a call and need to add a third person to that call:
- Click on the Conference key

Once you do so, the current call will be put on hold.
2. Dial the extension that you wish to add to your call, and when you get an answer, click on the Conference key again to merge both calls into a conference call.
3. If the recipient of the second call didn’t answer your call or didn’t want to join the call, click on the Line key next to the previously held call displayed on the main screen to reconnect again to that call.
Whilst held the caller hears music.
1. To login to your voicemail, press the Message key ![]()
2. After a small ringtone, you will be asked to enter your password.
3. Follow the voice prompts to playback your voice messages.
If you need to reset your password, open an IT Ticket.
CrowdStrike
Falcon CrowdStrike is an Endpoint Detection and Response (EDR), which is the evolution of the known antivirus technology.
EDR is considered the next-generation anti-virus as it is the replacement for the traditional known anti-virus solutions that became obsolete and inefficient in detecting and preventing attacks and malware.
This EDR technical offering is powered by machine learning to ensure that breaches are stopped before they occur/spread, even if it is seen for the first time.
For the Crowdstrike FAQs, click here.
Yes, Endpoint Detection and Response (EDR) is the next generation of the traditional antivirus.
It has normal anti-virus capabilities; this platform has much more ability to detect modern attacks based on machine learning and artificial intelligence.
Examples of other universities that use CrowdStrike in specific (aside from universities that use other EDR brands):
Ransomware and advanced cyber attacks became very hard to detect and contain. The expected AUC loss cost is huge if it gets a successful ransomware attack. Egyptian and International laws mandate organizations to set the proper controls for protection. Accordingly, the EDR/Crowdstrike became essential for maintaining AUC security and compliance.
It's available to all AUC devices’ that are in the custody of faculty and staff, as well as all AUC servers and digital services. In general, all AUC critical/important digital services should have Crowdstrike. AUC services, data and research are our focus.
Personal devices owned by faculty/staff/students, lab devices and pure isolated build-and-destroy environments are currently excluded.
You can open a ticket with IT Support or contact the IT support team in your office/area/department.
CrowdStrike is a lightweight program on your machine with a size of less than 5 MB. Once CrowdStrike is installed, it proactively scans for threats on your machine without running scans manually. CrowdStrike automatically scans any flash memory/external storage attached to the device without any initiation from the user. CrowdStrike will not alert you when a threat is found or blocked; it will alert the information security team to do an adequate assessment, respond, and notify/alert you. There is no system tray icon for the software; CrowdStrike runs in the background. Updates for CrowdStrike are done automatically, so there is no need to update manually.
No, CrowdStrike is not designed to open and read your files; Crowdstrike does not access the content of any:
- Documents
- Email messages
- Websites
- Web pages that are viewed/visited
- Instant messaging/chat communications
Also, Crowdstrike is not designed to track and report details of your online activity unless they expressly and explicitly threaten the computer; accordingly, as part of securing it, the team will trace the hacker/malicious file online activity.
Visit CrowdStrike FAQs to know more about the data sent to the CrowdStrike Cloud.
University statements about CloudStrike Cloud:
University of Michigan: Endpoint Protection: Data Collection, Sensitive Data, and Privacy
Cornell University: Crowd Strike Frequently Asked Questions
University of Illinois: Endpoint Security, CrowdStrike, Frequently Asked Questions
Crowdstrike does not access the content of any:
- Documents
- Email messages
- Websites
- Web pages that are viewed/visited
- Instant messaging/Chat communications
CrowdStrike looks for suspicious processes and programs. To do this, it records details about the username that has logged in on the machine, what programs are run, and the names of programs/files that are read or written, and records network activity.
The above-mentioned activities set are done to identify malicious software installation/action, ransomware/encryption action, data exfiltration, remote control and so on. It analyzes the behavior of executable programs/scripts to detect malicious code or connections to IPs that are used by hackers.
For example, if you log in and open a Microsoft Word document called “example.docx,” CrowdStrike Falcon will:
- Record the computer name and logged-in user name
- Record that the Word application was run and gather some details about the Word program itself
- Record the file name “example.docx” but will not access or provide any information about the content of that file
For more information about CrowdStrikehave access to the contents of my files or track my online activity; check the previous question in the FAQs.
Visit CrowdStrike FAQs to know more about the data sent to the CrowdStrike Cloud.
University statements about CloudStrike Cloud:
University of Michigan: Endpoint Protection: Data Collection, Sensitive Data, and Privacy
Cornell University: Crowd Strike Frequently Asked Questions
University of Illinois: Endpoint Security, CrowdStrike, Frequently Asked Questions
No, CrowdStrike is unlikely to affect the computer’s performance. It is also designed to be lightweight and not interfere with the normal use of the computer. Rather than scanning entire hard drives for viruses, CrowdStrike more efficiently detects patterns of suspicious program activity to identify possible malware. And It uses a negligible amount of bandwidth to function.
- CrowdStrike complies with GDPR requirements for properly handling personal data collected and stored in the CrowdStrike Falcon platform.
- CrowdStrike offers a platform and cloud security, intelligence subscription services, professional services, and more to organizations looking to achieve GDPR compliance.
In addition to adhering to post-Schrems II lawful transfer mechanisms, as detailed in the data protection agreement, CrowdStrike continues to participate in and has certified compliance with the EU-US Privacy Shield Framework and the Swiss-US Privacy Shield Framework. CrowdStrike is committed to subjecting personal information received from the European Economic Area (EEA), the United Kingdom, and Switzerland in reliance on each Privacy Shield Framework to the Framework’s applicable Principles.
To view the CrowdStrike compliance certification list, click here.
- PCI DSS V3.2
- Cybersecurity Maturity Model Certification (CMMC)
- FEDRAMP
- Criminal Justice Information Services (CJIS)
- EU-U.S. and Swiss-U.S. Privacy Shield Frameworks
- General Data Protection Regulation (GDPR)
- HIPAA
- NIST SP 800-53 REV. 4
- FFIEC
- VPAT
- ANTI-MALWARE TESTING STANDARDS ORGANIZATION (AMTSO)
- CLOUD SECURITY ALLIANCE (CSA) SECURITY, TRUST, & ASSURANCE REGISTRY (STAR) ATTESTATION
- AV COMPARATIVES TESTING
- SERVICE ORGANIZATION CONTROL 2 (SOC 2®)
- NSA-CIRA
To view the CrowdStrike compliance certification list, click here.
The Crowdstrike solution runs from a Crowdstrike-owned cloud; accordingly, the logs/evidence of all administrative activities are tamper-proof/can’t be deleted. Also, access to Crowdstrike solution is protected and recorded through a privileged access management solution against any possible violations, abuses, and sabotages. Access to the Crowdstrike solution is restricted by AUC to a small, designated team only.
Modern attacks and hackers’ first action when they hack any device is to disable any Antivirus/Protection software on that device. Accordingly, CrowdStrike is designed with protection guards against this to prevent potential attackers from removing it from the computer. Same as most anti-viruses solutions. You will need to open a ticket with IT Support with a clear justification for the removal request.
Software Installation Guides
- To access MATLAB, log in to MathWorks.com and download your software for free..
- For detailed instructions on how to create an account and how to install MATLAB, visit Matlab Installation Guide PDF
For Adobe, SPSS, Endnote, and all other educational discounted resources, please visit the official OnTheHub Portal and search for your needed software.
- For Adobe, SPSS, Endnote, and all other educational discounted resources, please visit the official OnTheHub Portal and search for your needed software.
- To know more about how to create an account and search for software. Check OnTheHub Guide PDF
BigFix
hcl® BigFix is a suite of products that provides a fast and intuitive solution for IT management and allows AUC to collect security reports from managed computers. The collected data does not include any direct personal identifiers (email, calendar events, contacts, personal files) from your laptop or desktop computer.
BigFix collects information about the managed devices that include data related to hardware, running operating system, installed software, the configuration of the devices, network connectivity, and BigFix Client. You can find detailed information about retrieved data on the BigFix Retrieved Properties List.
The American University in Cairo respects your privacy, and BigFix does not collect any direct personal data (email, calendar events, contacts, personal files, and so on) from your laptop or desktop computer.
No, BigFix is not used for remote support in any way, but instead, AUC uses:
- VNC for Classrooms and Labs support
- Zoom for office support
Remote Support
While opening an IT ticket, you can leave a note stating that your preference is to have your support session remotely. Your request will be subject to technical assessment, and if feasible, an IT staff member will contact you to arrange for holding the session remotely.
The allowed actions while in a remote support session are:
- Asking the user to restart if needed
- Asking the user to control or open applications or webpage for testing
- Asking the user permission to send a file to his computer
Note that IT staff members will never ask for sharing or disclosing users' credentials or any confidential information during remote support sessions.
Below are the applications allowed for remote support and their zone of usage:
- Classrooms: VNC
- Offices: Zoom
Yes, there is an AUC IT Procedure for Remote Access that prohibits using remote support software without user consent. Any violation of this procedure will subject the violator to sanctions up to dismissal. Only defined and limited IT staff has the right to use the remote support feature. Any exception is not allowed, and if requested, it will need senior management's explicit and documented approval.
Self Service Portal
1- First user has to go to the Link : http://10.2.49.20:9999/showLogin.cc he/she will show below screen.
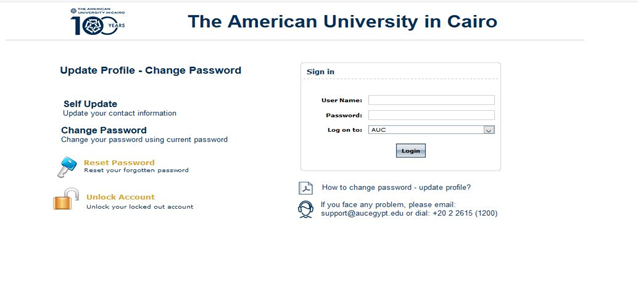
2-User has to enter his/her username & password in sign in field
3-After user has logged in he will got the disclaimer agreement as shown below
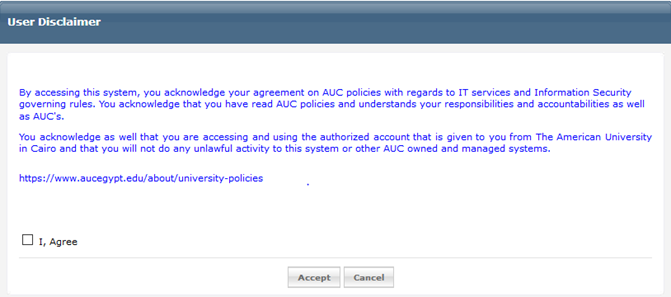
After user check box that he/she agreed the disclaimer he will then got a welcome message box and enforcing him/her to enroll the security questions by him/her self so be able to reset /unlock his/her password. “If user didn’t enroll the security questions, he/she won’t be able to reset his/her password”. Welcome box message is shown below
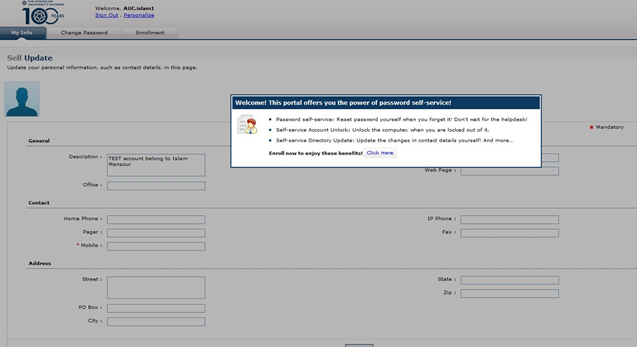
4- User has to click “Click Here” link shown in the bottom of the welcome box as shown above.
5- User will forward to the self-update page, so he/she could add/change his personal info in Active Directory and then click update. AS shown in below screenshot.
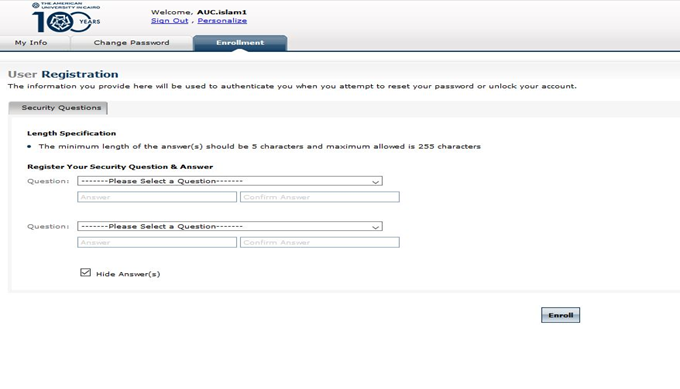
6- Then user should go to Enrollment tab to define his/her security questions.
1- User should define his/her enrollment security question to be able to reset his/her password. As shown below.
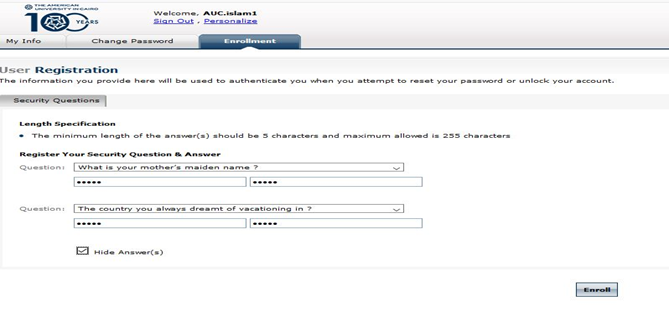
2- After user defined his /her security questions, he should click Enroll button in the right bottom of the page. As shown below.
1-First user has to go to Link : http://10.2.49.20:9999/showLogin.cc he/she will show below screen.
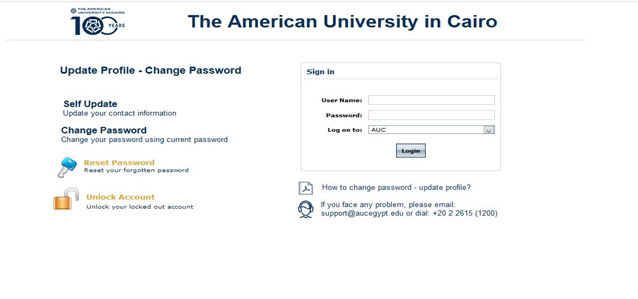
2-User will go to reset password in the left middle of the page as shown above.
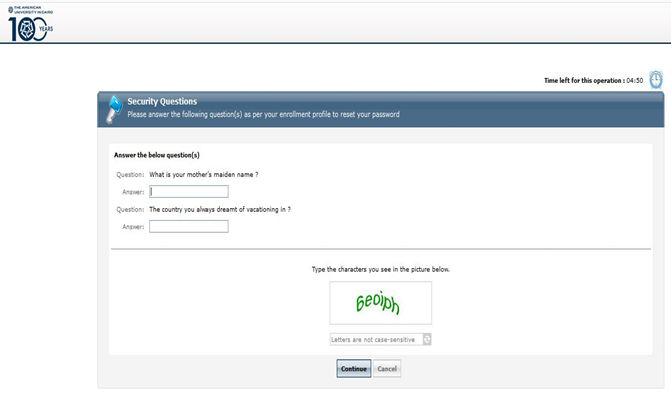
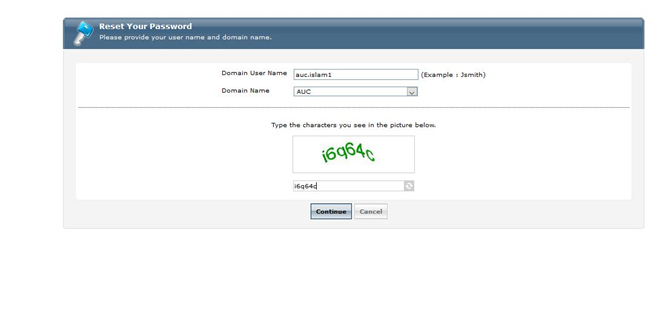
3-User will get the below page to enter his/her account in “Domain User Name “filed and to enter to security code below and hit continue.
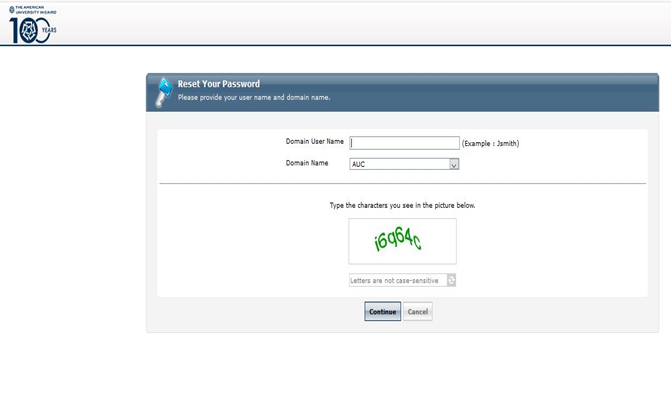
4-User will be asked to provide security questions he/she was defined and to enter to security code below and hit continue as shown in below screen.